Advanced Wi-Fi Attacks Using Commodity Hardware
Abstract
We show that user-modifiable firmware can be used to implement low-layer attacks against Wi-Fi. Hence cheap off-the-shelf Wi-Fi dongles can be used to carry out advanced attacks. We demonstrate this by implementing five low-layer attacks using open source Atheros firmware. The first attack consists of unfair channel usage, giving the user a higher throughput while reducing that of others. The second attack defeats countermeasures designed to prevent unfair channel usage. The third attack performs continuous jamming, making the channel unusable for other devices. For the fourth attack we implemented a selective jammer, allowing one to jam specific frames already in the air. The fifth is a novel channel-based Man-in-the-Middle (MitM) attack, enabling reliable manipulation of encrypted traffic.
These low-layer attacks facilitate novel attacks against higher-layer protocols. To demonstrate this we show how our MitM attack facilitates attacks against the Temporal Key Integrity Protocol (TKIP) when used as a group cipher. Since a substantial number of networks use TKIP as their group cipher, this shows that weaknesses in TKIP have a higher impact than previously thought.
Source Code
All the code is hosted on github. This includes a public VMWare image with the modified drivers and firmware preinstalled. Simply download and start it, plug in your WiFi device, and start experimenting!
A few remarks are in place:
- The most important additions to the firmware are located in firmware/target_firmware/wlan/attacks.c. In particular this includes the code for the reactive jammer.
- Most driver modifications are located in drivers/drivers/net/wireless/ath/ath9k/htc_*.c. In particular we added several new entries to debugfs in the htc_drv_debug.c file.
- The channel MitM attack and accompanying TKIP attack is included the tools repository. There is also a tools that provide a command-line interface for the reactive jammer.
Network Traces
We have three type of traces, all corresponding to our example attack on WPA mixed mode:
- The trace generated by our `channelmitm` tool: attack_mitm.pcap.
- Traces created by capturing input and output of the network interfaces of the attacker: attacker_1.pcap and attacker_13.pcap. These represent the interface on channel 1 and 13, respectively.
- Traces created by an external monitor device of channel 1 and 13 during the attack: monitor_1.pcap and monitor_13.pcap, respectively.
The usage of an external (independent) monitor is important because the traces created by the attacker are done at the OS level. Hence injected frames might have undergone (minor) modifications by the firmware before being transmitted. Additionally not all management packets are captured (in particular ACKs of injected frames are not included). Our independent monitor device captures all these missing (or potentially modified) frames.
Note: these network traces have been filtered to remove potentially sensitive information. For more details see the filters used.
Example
We recorded an execution of our attack against WPA mixed mode. The network trace corresponding to this attack can be viewed online on cloudshark. This network trace has been filtered to only include packets relevant to our attack. The network activity graph on cloudshark beautifully summarizes our attack on WPA mixed mode:
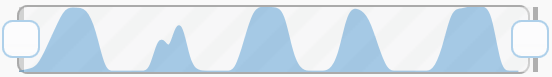
For each of the first four peaks of network activity, both clients are attacked right after each other. This decrypts 8 bytes of the ARP request. The time between each peak assures clients will not send more than 1 MIC failure report per minute. During the final peak of activity we decrypt the final 4 bytes. Here we no longer wait one minute between attacking a specific client. This causes both clients to detect two MIC failures within one minute. Hence they disconnect from the AP. However, this is no problem, since we now decrypted the ICV and MIC, and the AP is unaware of our attack. Since the ICV and MIC is decrypted we can calculate the MIC key.
The full execution of the attack is shown in this video: